
Hi, I'm Eric.
I’m an avid world traveler, photographer, software developer, and digital storyteller.
I help implement the Content Authenticity Initiative at Adobe.

Hi, I'm Eric.
I’m an avid world traveler, photographer, software developer, and digital storyteller.
I help implement the Content Authenticity Initiative at Adobe.
10 October 2023
This week I’m attending the 37th biannual Internet Identity Workshop, in which a few dozen of the world’s leading experts on digital identity and credentials gather and a couple hundred more of us do our best to keep up and learn from them.
In my work at Adobe I help define and implement the Content Authencity Initiative. CAI defines itself as:
… a community of media and tech companies, NGOs, academics, and others working to promote adoption of an open industry standard for content authenticity and provenance.
We are particularly interested in enabling content creators to identify themselves as the creators of their content and credibly refute false claims of authorship on their behalf, which is why I am attending this conference for the third time. This is my first time attempting to describe it in real time as the conference proceeds.
IIW is held at the lovely Computer History Museum, which recounts the formative years of our tech industry. CHM is located in Mountain View, California, right in the heart of Silicon Valley.
I’ll share a few photos of the venue and the conference. My non-technical friends might want to bow out after this section as it will rapidly descend into lots of deep geek speak.



IIW is conducted as an “unconference,” which means that there is a pre-defined structure to the conference, but not a predefined agenda.
There are several variations on how the agenda gets built at an unconference. In IIW’s case, there is an opening meeting on each morning in which people stand up and describe sessions they’d like to lead that day. Then there’s a mad rush to schedule these sessions (see photo below) and we all choose, in the moment, which sessions to attend.





You might think that not having a predefined agenda would mean that the topics that occur could be flimsy or weak or low in value. In practice, the opposite is true. Both times I’ve attended this conference so far, I’ve had to make very difficult choices about which sessions not to attend so I could attend something else which was also very compelling.
Last time (in April), I managed to schedule a weekend to myself disappearing on the Mendocino coast to decompress afterward. For those of us who are introverts, I highly recommend scheduling some kind of downtime like this afterward. (I talked to almost nobody for four days after IIW and it was perfect.) This time, I’m headed home for some important family time, so no decompression buffer.
And, with that, here is my description of the sessions I’m attending this time around:
Karla McKenna, Head of Standards and Managing Director of GLEIF Americas

Vendors moving through vLEI qualification program: roughly 8 vendors in progress now.
SDK in progress. Release candidate will be shown during demo hour. SDK includes:
OORs (Official Organizational Roles) added in June 2023, lists 2000+ distinct kinds of official roles that are known to the varying forms of legal entities across 89 jurisdictions. (See photo below.)

vLEI adding support for did:webs method.
KERI, ACDC, CESR officially moved to ToIP Foundation. GLEIF is driving standardization for this tech through W3C Verifiable Credentials working group.
QVIs have to disclose rate of issuance. It’s early days overall in vLEIs, but some sectors (notably telecommunication) “reaching critical mass.” Still working on issuing at scale.
Selling point is international verifiability.
GLEIF under regulatory oversight since formation. Roughly 70 global regulators, largely in financial sector because that was the reason for creation.
GLEIF looking at vLEI as a method for enhancing adoption of LEI. Private sector reporting to public sector is a huge use case.
European Banking regulator (EBA), which regulates several thousand banks in the EU, did proof-of-concept with vLEI for signature and EBA verified those signatures. Initial indications about this are very promising.
Changing the narrative to “organizational identity.” Moving from technical capabilities to creating verifiable proof that Person X is a legal representative of Organization Y. Timothy Ruff wrote about this earlier this year: The Dawn of Organizational Identity, Part 1: Identifiers and The Dawn of Organizational Identity, Part 2: Credentials.
Telecomm businesses approaching Provenant and other QVIs to prove authority to communicate on behalf of organization.
Example: If you are running a text messaging campaign, your organization has to be vetted for authority and quality of message. Important in this case to know who are the people that are going to be asking for privileges to execute that campaign. This gets increasingly interesting as tasks such as this get delegated across companies. (Consider a major brand hiring a third company to execute the text messaging campaign on their behalf. How does the telco know whether to accept those messages as accurately representing the original brand?)
As mentioned in the intro, IIW almost always presents difficult choices about which sessions to attend. I look forward to reading the notes from these sessions which competed with this one:
Timothy Ruff, GP, Digital Trust Ventures

Timothy starts by replaying The Four Horsemen of SSI from Identiverse 2023 by Jeremy Grant.
The key points of Grant’s presentation:
Let’s not build identity for the 1%.
Question: How many of you use a password manager? (Most hands went up.)
Password management onboarding is awful. Once you’re there, there’s no going back!
Hmmm … managing passwords is much like managing keys. Once you turn it over to trusted software, password vs key is not that different. You can manage thousands of keys this way.
Ummm … there are authoritative sources participating in SSI space. (Looks around room …)
Timothy sort of agrees with this but shifts the thinking here.
Once you’ve shared information, it’s shared. There’s no unsharing.
There are lots of unintentional and non-consensual data leaks (face-recognizing cameras, using credit cards for purchases, etc.).
Huh. Interesting take: Stop trying to conceal data. Stop worrying about PII. Corraling data back is a lost cause. It’s too easy to re-identify data sets that have supposedly been anonymized by correlated with other data.
Legal mechanism for preventing info sharing of this sort is a non-disclosure agreement. Those are very heavyweight.
What if … NDAs were streamlined, digital, and digitally signed before data was disclosed?
Now we’re enforcing limited data sharing by legal terms, not technical. Something like this is built into KERI stack via ACDCs.
Timothy: “Privacy is dead. Long live confidentiality.”
You don’t.
This is actually valid. Defaults win.
The meals at IIW are surprisingly good for conference food.


Wallets are critically important.
Speaker was in China recently and couldn’t pay for food without Chinese wallet app.
OWF is not about creating standards. Building upon standards built by Open ID Foundation, FIDO, etc.
OWF advocates for open-source software to build wallets for cost, time, and security, and interoperability reasons.
In April, OWF had 26 corporate members and no code. Today, 52 members including Google and Microsoft. Now have a lot of code.
OWF seeking members to join technical community. Slides will be made public.
Google proposing to contribute Android Identity Library to OWF.
Agenda shifted to what can you contribute to OWF, which isn’t particularly relevant for me. I departed at this point.
Open discussion about UX challenges in SSI.

Issues raised:
Moderator Q: Who has solved a serious UX challenge already?
One answer: “If you get the UX right for a new technology, it will not be adopted.” Hmmm.
Sukhi Chuhan (Senior UX Designer at Ontario government): Expectation is that VCs for end users needs to be about ease of use. Make it more and more like what you can do with physical IDs.
If you’re creating a new digital wallet product, you are competing with free and built-in from Apple and Google.
Terminology has a big impact. Example: “biometric authentication” scares users, but “Touch ID” and “Face ID” don’t.
Remember accessibility. For example, people with impaired vision can’t really use QR codes. Also, some people with disabilities and also children may have caregivers or guardians who need to be able to act on their behalf.
Most users will pick utility over sovereignty any day.
Some resistance to using platform-provided wallets due to perception of security concerns and hackability.
Audience Q: How do you present VCs in a way that’s digestible?
BC wallet specifically avoids showing information on screen. They want to force the info to be transmitted digitally and displayed on the verifier’s device, not the holder’s device. On-screen display is easily faked by the credential holder.
As is so often the case, this was one of the best-attended sessions at IIW.


Recap of this blog post from ToIP: Mid-year Progress Report on the ToIP Trust Spanning Protocol.
Seven pillars of trust spanning protocol:
Believe the trust layer for the Internet will require a new spanning layer, akin to IP for traffic itself. Requires a new form of address, which they call Verifiable Identifier. These are commonly DIDs, but not necessarily.
VIDs can also incorporate centralized identifiers. For example, HTTPS address or X.509.
A ToIP identifier must be cryptographically bound to private keys and discoverable.
Talking about ESSR (Encrypt Sender’s key then Sign Receiver’s key) pattern. That is a 50-page white paper; it’s well summarized in this blog post by Neil Madden: Public key authenticated encryption and why you want it (Part II).
ESSR allows you to build from zero trust to verifiably authentic with an option to add encryption.
Remember that privacy has two aspects:
If I trust you (by sending you data that you can decrypt), there’s little I can do technically to prevent you from misusing that data. Legal and contractual obligations are more relevant here.
But … we can prevent third parties who don’t have the right keys from spying on the data or even breaching “correlation privacy” which establishes a pattern of communication between two parties.
Every ToIP connection provides at least partial correlation privacy.
Using intermediaries allows full correlation privacy. From a protocol design standpoint, it requires one more level of nesting. But no further “onion” style routing is required.
Nested channels also allows you to create an unlimited number of communication contexts between patterns.
ToIP wound up choosing CESR.
Basic idea was not to fight the protocol war between text and binary representations. CESR allows you to switch back and forth in composable and predictable fashion without invalidating the signature.
All three of the VID-to-VID protocols (DIDComm, KERI, and DWN) include frameworks to support higher-level protocols designed to accomplish specific trust tasks.
Examples of trust tasks are:
Those trust tasks (layer 3 of the ToIP stack) enable an infinite set of applications on top of that (layer 4 of the ToIP stack).


Open discussion led by Adrian Gropper (the volunteer CTO of the non-profit Patient Privacy Rights Foundation). What do people want instead of digital identity?
Representative from Guardian Project: How do you have continuity and yet anonymity?
Usability and perceived security risk again is a topic.
California’s digital ID is dual-format (mDL and VC). Proof of age via VC. Look at TruAge, about to be integrated with point-of-sale systems, supported by age-restricted goods industries.
Organizational identity is nuanced and complex. Contractors, employees, vendors … all of these relationships require verification, trust, audit trails.
Many organizational identity considerations:

Organizations have a high stake in their identity. Can not trade-off security with anything else.
Lifetime of identifiers is critical.
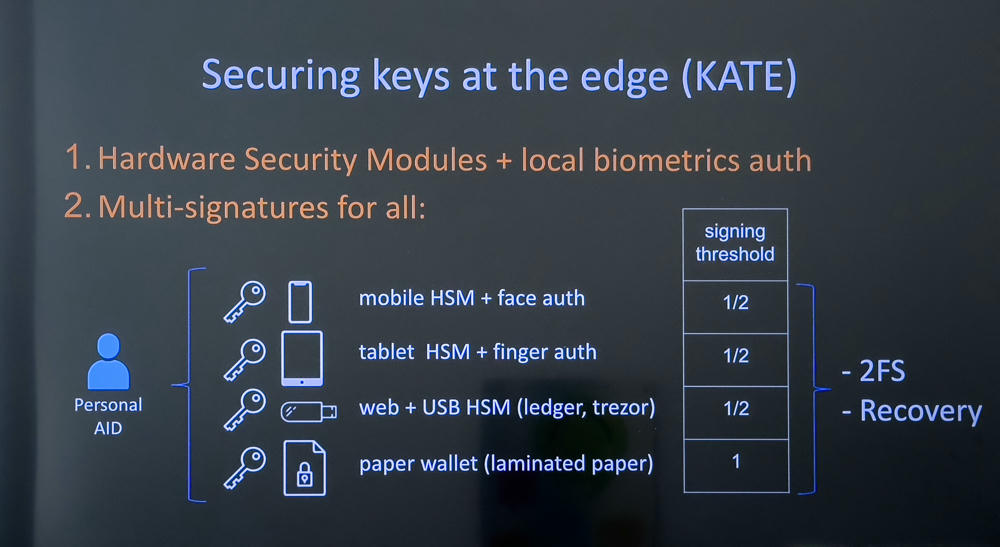
NEW: Securing keys at the edge (KATE). HSMs and/or local biometrics control access to keys. Using multi-sig gives you ability to recover access to personal AID.
New “signify” codebase helps with signing at the edge. Key event generation and signing, among other tasks.
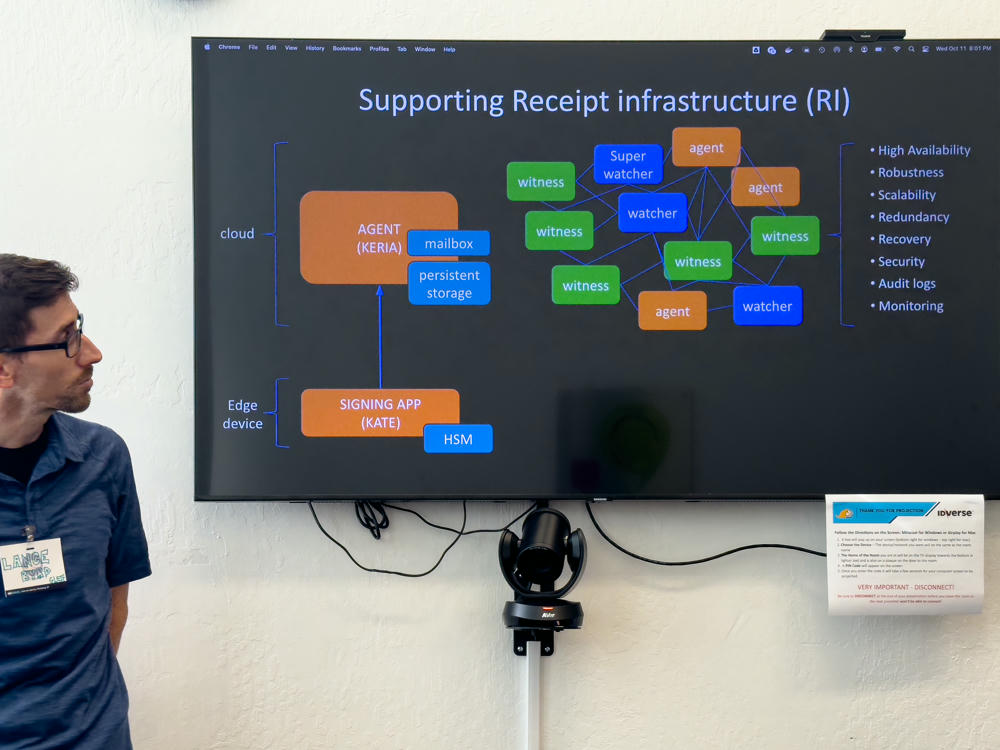
Audience Q: How much do witnesses cost? How do you find them?
A: Early days. Right now it’s the early adopters. Expect this to be commoditized. “We anticipate that there will be witness services.” Those are likely to be free for low/normal volume situations. If signing millions per month, then cost may need to be passed along.
ACDC means that vLEI credentials are chainable, end verifiable, attestable organizational credentials. Chainable means orgs can issue credentails for anyone from C-suite to individual employees.
IPEX (VC issuance and presentation exchanges). Exchanging of chained credentails facilitates legally-binding agreements and contractually-protected disclosures.
I came in late. Justin was giving some background explanation of NIST SP 800-63-4 “Digital Identity Guidelines,” which is currently in “initial public draft” stage.

He was explaining subject -> CSP (Credential Service Provider) -> IDP (ID Provider) -> relying party interaction in NIST terms.
“IDP is played by the wallet. This is where things start to go funny.”
NIST uses different terminology from SSI/VC community. Approximate translations of a few common terms:
I’m a bit out of my element here because my work doesn’t particularly overlap with NIST (or at least hasn’t so far), so it’s mostly interesting to see how things map from one world to another.


Define ephemeral privacy: Privacy “exists” but is easily undone because “de-anonymized” data is easily re-correlated.
It’s effectively trivial to re-identity individuals from de-anonymized data sets.
Define privacy washing: De-anonymize data to the point where it can legally be re-shared. But … there are holes. You may have intentionally or unintentionally left hooks for yourself or others to re-correlate and re-identity individuals in that data set.
Timothy argues that ZKPs and AnonCreds (which his team helped develop) are no longer useful. So easily defeated as to be not worth the effort.
“We aren’t saying privacy is dead. We believe the future is confidentiality …” using legal tools rather than technical tools.
Privacy through obscurity is no longer worth it.
New focus: Make legally-binding personal terms and conditions easily exchanged.
Joyce Searls points toward IEEE standard P7012 which is a way that individuals can exchange terms. Timothy: “It is exactly that.” ACDCs enable that technically.
Sam Smith: “People are falsely believing that they have a false sense of security with selective disclosure.” This is no longer true.
Description of how little info it takes to re-identify data.
Privacy washing exists because the legal frameworks are years behind the technology.
FTC issued a report last year that says k-anonymity is no longer sufficient for privacy. Example given of how cell-phone location data can be used for re-identification. Another example: social graphs could be reconstructed via the so-called anonymous identifiers in Covid contact tracing apps we had a year or two ago.
Anyone sophisticated enough to verify a ZKP is almost certainly sophisticated enough to perform a re-identification attack.
ACDCs have the ability to support contractually-protected disclosure. This is the technical part that enables a quick and frictionless agreement of terms. The mechanics are there to do this. Now need policy that follows that.
Daniel Hardman isn’t present, but it sounds like his work in the earlier-mentioned IEEE standard builds upon this.
Timothy Ruff: “Timing is everything. I think there is a hunger for privacy like the world has never seen. So our timing is good to introduce these things to the world.” And tech is converging around this.
Audience Q: Is this a US problem or a worldwide problem? Audience answer: Same issue (resale and re-correlation of private data) exists worldwide, only varying by degree country to country and even state to state within the US (e.g. CCPA in California).
Presentation Exchange can do a lot of different things.
Starts by summarizing content posted at What does Presentation Exchange do and what parts of it do we actually need? on Mike’s blog, Mike Jones: self-issued.
Much active discussion about combining credentials issued from different sources (e.g. university degree + drivers license + professional license).

I came in late. Drummond was walking through some existing SSI glossaries that already existed and why ToIP is building its own.
On eSSIF-Lab Glossary (EU funded), they also have a mental models section.
Glossary is currently available as an early draft on Google Docs. Sounds like they will migrate it to MediaWiki or similar later this year.
Brian Richter did a bunch of tooling to make this feasible and to assist in the translation from GitHub wikis to Google Docs. Looks like a tremendous amount of work done to make editing and viewing accessible to people who do and do not prefer working with GitHub.

Just a week or so ago, I first heard the term “verifiable identifier” when Drummond Reed appeared on episode #60 - Trust Spanning Protocol: Seven Key Pillars of Matthieu Glaude’s excellent SSI Orbit podcast.
This is described in the ToIP Technology Architecture Specification in section 6.4 titled ToIP Identifiers. I’m happy to hear that ToIP is recognizing that there’s value in identifiers that can be independently verifiable, regardless of how they are issued (i.e. in a decentralized or centralized fashion).
It looks like this is currently a conceptual unification between DIDs and centralized identifiers (X.509 and similar) and not yet a technical spec that describes a protocol format that allows you to express “DID or X.509 or …” but that this is an area of active interest from ToIP.
Full proceedings from the conference are typically available a few weeks afterward. I’ll add a link when that becomes available.

Subscribe to my free and occasional (never more than weekly) e-mail newsletter with my latest travel and other stories:
Or follow me on one or more of the socials: